Cyber criminals are continuing to profit from the coronavirus crisis and have launched significantly more attacks since the outbreak of the pandemic. Even though many employees have now returned to their office workstations from their home offices, people are spending much more time at their computers when off work - to shop online, for example, or to order a delivery service for food. The exposure to attacks has become considerably greater due to the increase in online use.
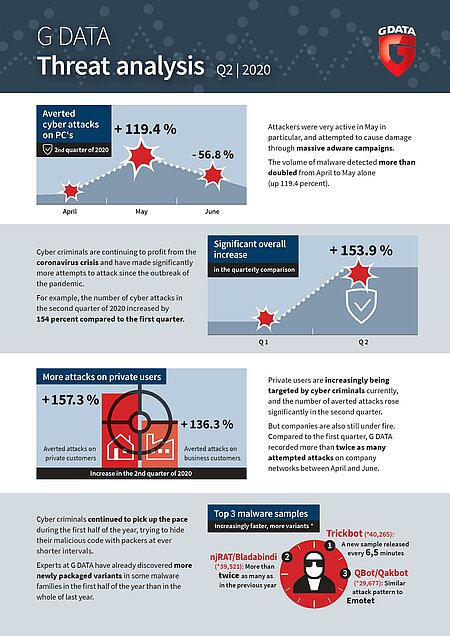
Massive increase: Number of cyber attacks increases by 154 percent in the second quarter
G DATA CyberDefense fends off major adware campaigns in May
The latest G DATA CyberDefense threat analysis shows that cyber criminals have continued to attack private users and companies on a massive scale in the second quarter. The cyber defence specialists from Bochum fended off more than twice as many attacks in May as in April.

Private users are being increasingly targeted by cyber criminals currently. . The number of attacks prevented rose by more than 157 percent in the second quarter compared to the first. But companies are also still under fire. The cyber security experts at G DATA recorded 136.3 percent more attempt attacks on company networks. Attackers were particularly active in May, and attempted to cause damage through massive adware campaigns. The volume of malware detected more than doubled from April to May alone (plus 119.4 percent).
Adware - advertising through the back door
In May, cyber defence specialists identified several major adware campaigns and stopped them spreading further. Even though at first glance it causes less damage than ransomware, users should not underestimate adware. This is because the malware collects personal data on things such as surfing habits - data that those behind it turn into money. The sharp increase is also due to the fact that developers make constant improvements to their adware. For example, they circumvent some of the antivirus programs or operating system restrictions. Another reason is that, in contrast to malicious malware such as ransomware, there is no need for elaborate technology to develop appropriate adware campaigns. The effort is minimal, with a maximum pay-off.
Malware Top 10 - new malware samples every second
Cyber criminals continued to pick up the pace during the first half of the year, trying to hide their malicious code from antivirus solutions with packers at ever shorter intervals. Experts at G DATA have already discovered more newly packaged variants in some malware families in the first half of the year than in the whole of last year. In the case of Trickbot, the numbers have almost tripled. On average, criminals published a new Trickbot sample and attempted to infiltrate computers and networks every 6.5 minutes. The remote access Trojan njRAT / Bladabindi has as many new samples after just 6 months as in the whole of last year. And Emotet, the cyber criminals’ all-purpose weapon, was very active at the beginning of the year, before growing quieter from February onwards.
The Malware Top Ten at a glance:
| Position | Name | Variants | Type |
| 1 | Trickbot | 40265 | Malware Distributor |
| 2 | njRAT/Bladabindi | 39521 | Remote Access Trojaner |
| 3 | QBot/Qakbot | 29677 | Remote Access Trojaner |
| 4 | Emotet | 27804 | Malware Distributor |
| 5 | RemcosRAT | 24845 | Remote Access Trojaner |
| 6 | SakulaRAT | 23158 | Remote Access Trojaner |
| 7 | BlackShades | 21241 | Remote Access Trojaner |
| 8 | Tinba | 20881 | Banking-Trojaner |
| 9 | AgentTesla | 19060 | Information-Stealer |
| 10 | AMRat | 17149 | Remote Access Trojaner |
The Malware Top 10 is dominated by Remote Access Trojans (RATs). Seven of the ten families are RATs that allow remote control and administrative control of a third-party computer without the user noticing. The manipulation capabilities range from spying on passwords and reading confidential data to deleting the contents of the hard drive or encrypting files.
Qbot assumes Emotet behaviour
One newcomer to the ranking is Qbot. Currently, this RAT uses an attack pattern that was previously only associated with Emotet. The malware adds a new entry to an email conversation that already exists, so the recipient trusts the authenticity of the message and clicks on the link contained in the email. This link leads to a hacked website, from which further malware is downloaded into the company network. Qakbot has been known since 2007 and has gradually developed - similar to Emotet - into an all-purpose weapon for cyber criminals. The original banking Trojan has additional worm elements and now acts as a credential stealer. Attackers use it to copy and subsequently misuse access data.
Coinminer - the performance stopper in the PC
In the first half of the year, G DATA also noticed an increase in Coinminer activity. Cyber criminals use the computing power of third-party computers to generate crypto currencies such as Bitcoin, Monero and Ethereum. More than 107,000 samples from various Coinminer families were identified - one sample every 2.4 minutes on average. Likewise, coinmining is not a new cyber threat. It has been around for several years at this point. Website operators and criminal intruders earn money with it, while users have to pay for the increased energy costs. To add insult to injury, their computers now have limited performance. This decrease is due to the activity of the coinminer, resulting in slow reaction times, unusual network activity or crashes and frequent reboots.
Conclusion: No sign of a let-up
Cyber criminals use a variety of methods to infiltrate corporate networks and private computers and to misuse them for their own purposes. They often take the path of least resistance and exploit gaps in operating systems or applications. “Humans also continue to be a gateway for attacks when they click on links in phishing emails or open attachments containing malicious code,” warns Tim Berghoff. “Modern endpoint protection is therefore only half the battle against cyber attacks. Attentive employees who can recognise such dangers and report phishing attempts are just as important.”